Cloud based solutions are continuing to grow in popularity. This is largely due to economic reasons, namely the personnel and resources required to stay on top of the new technologies and ever-changing threat landscape. blueEHR cloud-based solution enables companies to focus on their core business of caring for patients by leaving the technical aspects of the EHR application to the experts who really understand the latest technologies to keep the system running efficiently and changes in user behavior affect security vulnerabilities.
The cloud is not new. Businesses have been using remote or off-premise based services via the Internet for many years. When you use a cloud-based application, in this case Hosted OpenEMR, you are accessing the system via the Internet where the application is hosted in shared resource environment as opposed to being provided from your own on-premises servers. Cloud services are designed to provide easy, scalable access to the applications resources and services, which are managed by a 3rd party provider. A cloud service can dynamically scale to meet the needs of its users, and because the service provider supplies the hardware and software necessary for the service, there’s no need for a company to provision or deploy its own resources or allocate IT staff to manage the service. Popular examples of cloud services are web-based e-mail services, hosted office suites, and document collaboration services.
Currently ZH Healthcare is an authorized Business Associate of Amazon AWS and utilizes Amazon’s AWS Cloud as our data center infrastructure provider. Amazon is the pioneer in the field and has developed a reliable and flexible infrastructure that easily supports health care applications in a manner consistent with HIPAA and HITECH.
It’s a better business strategy. Spend time working with your patients, not your patient healthcare software. When your software is installed in your office, you have to deal with potential interruptions such as power outages, software upgrades, hardware failures and human error. With the software installed in the cloud, we upgrade the software for you without disrupting your practice. The cloud infrastructure is built on redundancy, meaning that your system is always available, even if there is an outage on our end. The services are designed so that outages are transparent to the users and all services remain available. It’s Scalable. Over time your EHR system will grow largely due to the increasing amount of patient data and additional improvements in the application software that may require more computing power. This will require additional computing resources in order to keep performing efficiently. On the cloud we can add more servers with the push of a button and will be transparent to you. This eliminates the need to buy additional costly hardware and perform ground-up configuration and disruption that would be required with an in-office solution to keep your system running. It’s Secure. With the increasing threat from hackers, both foreign and domestic, patient information is becoming more of a target and harder to secure. A local installation (in your office) requires extra attention to detail to keep secure. When you install the system in your office, you take on the responsibility of making sure the environment is safe from unauthorized access. By using our cloud-based solution you benefit from infrastructure that is already in place to provide both security benefits such as a private IP network isolation, encryption, server load balancing and automated backups. The following diagram describes the high-level architecture of the blueEHR System.
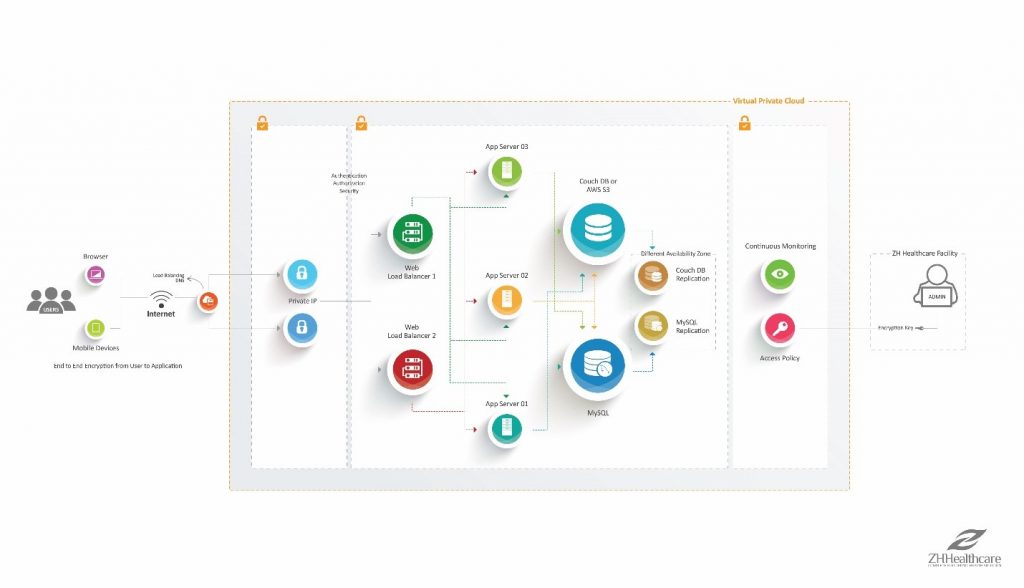
It is a fact that Internet connectivity and the cloud environment are subject to outages just as an in-house system is also subject hardware or software failures. We don’t have control over the Internet connectivity, however we can minimize the possibility of the system being unavailable due to hardware or software problems. In a cloud-based system there are highly skilled technicians supporting the infrastructure 24/7 monitoring it to keep it at its best condition. blueEHR utilizes server load balancing. Server load balancing means that there are two or more servers for every piece of the application software. If one of the servers experiences a malfunction due to hardware or software problems, it is automatically removed from production to prevent it from causing impact to the service. When the issue is resolved, it’s automatically placed back into service. In addition to server load balancing, the databases that store the EHR application data are replicated to a “hot standby” in real-time. This means if a main database is unavailable for any reason, the system will use the replicated database. These fail-safes can be costly to put in place in an in-house system due to the additional storage and resources to administer and manage the system. With a cloud-based system, not only can you take advantage of ensuring your system has this protection, it is also more economical.
Backups are used, in the very unlikely event, to recover data after loss or corruption. All electronic protected health information (ePHI) and transaction logs are automatically backed up on a schedule allowing the ability to restore the data back to the point of the retention period. Instead of having to maintain an expensive onsite backup system and deal with tapes, backups are automatically performed within the cloud. These backups are periodically tested to ensure that they work. A backup solution that is not tested is no backup at all. Our backup policies include
There are security risks with cloud computing. However, in-house systems also come with risks. In the blueEHR cloud-based solution the advantage is the technical platform and infrastructure is managed and updated by highly skilled technicians who understand the most current security measures to secure the technical components of the hardware and software to thwart intruders.
Security is a shared responsibility with cloud-based systems. As a user of the system who interacts with private health information must put protocols in place for your facility. These protocols should cover facility, password, and use of devices that can leave the office. These protocols should cover what data can be stored on a computer or other device that leaves your office, travels with employees, or that is used for remote work of any kind. Patient health information and other information such as credit card data, and bank account particulars should never be stored on unsecured devices. Encryption protocols should be in place and encryption software should be installed to help protect your data against unauthorized access. ZH Healthcare systems are secured with password protection to prevent unauthorized. Audit logs of data access are available to ensure that data is available only with the appropriate security clearance. In addition we have included additional optional safeguards that may be implemented these include:
As the caretakers of your infrastructure, ZH Healthcare enforces restrictive systems access policies with a stringent policy for passwords, and network access. We maintain system logs and monitoring as a part of our enforcement of these policies.
Private IP network isolation is a fancy way of saying the servers with sensitive data do not have a way of communicating with the Internet directly. Think of it like a gated community. The only servers with access to the Internet are the gate towers in a gated community connecting private roads to the public roads. Security is managed via those servers, so that only requests from users who have been authorized and validated can make requests to the servers with private IPs. Direct connection to the servers with private information is not possible, and therefore more secure.
The public facing server application layer is set up with threat mitigation software that automatically guards against the most common hacker attacks such as brute force hacking attempts. The software undergoes periodic testing with a white-hat (good guy) hacking attempt to review for vulnerabilities that need to be patched to mitigate threats from unauthorized parties and maintain a robust security system.
Our framework embodies the years of experience and skilled knowledge to provide each customer with a reliable and secure system. The servers are all configured identically to enable the best performance, reliability, and with security in mind. Only essential services are running, and those that are not needed are disabled. This reduces the potential for unauthorized access due to vulnerabilities in other pieces of software that are normally enabled by default.
Encryption is used to protect the health information while it is in transit. The encryption process encodes the information in a way that unauthorized parties or hackers cannot read it. We use 2048 bit SSL encryption throughout the entire user session to better protect against security threats. In short, the larger the key size, the more computationally expensive it is for an attacker to use brute force to compromise the infrastructure. The US National Institute of Standards and Technology (NIST) recommends that organizations depreciate the use of 1024-bit keys by year-end 2013. While 2048-bit keys deliver greatly increased security, they also require significantly greater processing power than 1024-bit keys. This means in order to maintain application performance and availability organizations need to adopt new SSL infrastructure specifically designed for stronger SSL. Our infrastructure is already designed to provide the same level of performance (speed) and as technology evolves and security requirements change, we will continue to update and change to protect sensitive health information.
Your system is prepared for worst-case scenarios to ensure business continuity in the event of a disaster. Every component of the system is periodically placed into a “snapshot.” These snapshots can be used to start up a new component on any system to restore service quickly in the event of a disaster. This is in addition to the automated backups. In addition we provide the ability to for our customers to download their patient data on demand at any time. This may be done by logging into your blueEHR account portal then selecting and running the download report. This report can then be stored in another off-site location according to your in-house procedures to ensure the data is safely stored. This provides an extra layer of protection in the very unlikely event the cloud infrastructure becomes unavailable. The patient data may be loaded into an on-premise server with a community version of OpenEMR or other EHR system.